In the shadowy realm of cyber warfare, a previously undocumented threat has emerged, casting a pall over the digital landscape. Dubbed "Kapeka," this flexible backdoor has been sporadically detected in cyber attacks targeting Eastern Europe, with Estonia and Ukraine bearing the brunt of its clandestine operations since mid-2022. In this exposé, we delve into the depths of Kapeka, unraveling its origins, modus operandi, and implications for cybersecurity.
Origins and Attribution: Tracing the Footprints of Sandworm
The revelation of Kapeka stems from the meticulous research conducted by Finnish cybersecurity firm WithSecure, shedding light on the covert activities of the Russia-linked advanced persistent threat (APT) group known as Sandworm, alias APT44 or Seashell Blizzard. Microsoft corroborates these findings, tracking the same malware under the moniker "KnuckleTouch."
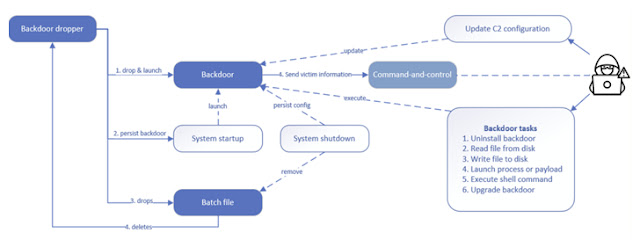
According to security researcher Mohammad Kazem Hassan Nejad, Kapeka represents a sophisticated backdoor meticulously crafted to serve as a versatile toolkit for its operators. Equipped with a cunning dropper, Kapeka infiltrates targeted systems, deploying a backdoor component before stealthily erasing its tracks.
Functionality and Capabilities: Unveiling the Arsenal of Kapeka
Kapeka's arsenal is as multifaceted as it is insidious. Microsoft's advisory paints a grim picture, linking Kapeka to numerous campaigns involving ransomware distribution and a plethora of malicious activities. From credential theft to destructive attacks, Kapeka serves as a conduit for nefarious actors to gain unfettered access to compromised devices.
Crafted as a Windows DLL written in C++, Kapeka conceals its malevolent intent behind a facade of authenticity, masquerading as a benign Microsoft Word add-in. Once embedded within the host system, Kapeka springs into action, establishing a covert communication channel with actor-controlled servers to receive commands and exfiltrate sensitive data.
The intricacies of Kapeka's operation extend to its adept use of the WinHttp 5.1 COM interface for network communication, facilitating seamless interaction with its command-and-control (C2) infrastructure. Leveraging JSON for data exchange, Kapeka demonstrates a level of sophistication characteristic of APT-level activity.
Propagation and Evolution: Unraveling the Mysteries of Kapeka
The propagation vector of Kapeka remains shrouded in mystery, although Microsoft's investigation hints at the exploitation of compromised websites using the certutil utility—a tactic emblematic of living-off-the-land binaries (LOLBins). This clandestine approach underscores the covert nature of Kapeka's operations, evading detection while infiltrating unsuspecting targets.
Moreover, Kapeka's lineage reveals conceptual and configuration overlaps with previously identified APT families, including GreyEnergy and Prestige. WithSecure posits Kapeka as a potential successor to GreyEnergy, suggesting a continuous evolution within Sandworm's arsenal of cyber weaponry.
Q. 1: What is Kapeka, and how does it differ from other malware?
Ans: Kapeka is a previously undocumented backdoor malware discovered in cyber attacks targeting Eastern Europe. Unlike other malware, Kapeka is highly flexible and serves as an early-stage toolkit for cyber attackers, allowing for long-term access to compromised systems.
Q. 2: Who is behind the development and deployment of Kapeka?
Ans: Kapeka has been attributed to the Russia-linked advanced persistent threat (APT) group known as Sandworm, also referred to as APT44 or Seashell Blizzard. The findings are corroborated by research conducted by Finnish cybersecurity firm WithSecure and Microsoft.
Q. 3: What are the main functionalities and capabilities of Kapeka?
Ans: Kapeka functions as a versatile backdoor with the ability to execute various malicious tasks, including stealing credentials, conducting destructive attacks, and providing remote access to compromised devices. It utilizes sophisticated techniques, such as masquerading as a legitimate Microsoft Word add-in and employing multi-threading for efficient task execution.
Q. 4: How does Kapeka propagate and infect systems?
Ans: The exact method of propagation used by Kapeka is not fully disclosed, but it is believed to exploit compromised websites using the certutil utility, a tactic commonly associated with living-off-the-land binaries (LOLBins). This stealthy approach enables Kapeka to evade detection while infiltrating target systems.
Q. 5: What steps can organizations take to defend against Kapeka and similar threats?
Ans: Organizations can bolster their defenses against Kapeka and similar threats by implementing robust cybersecurity measures, including regular system updates, network segmentation, and employee training on identifying phishing attempts. Additionally, leveraging advanced threat detection and response solutions can help detect and mitigate attacks in real-time.
Conclusion: The Ongoing Battle Against Cyber Adversaries
As the specter of cyber threats looms large, the emergence of Kapeka serves as a stark reminder of the ever-evolving nature of digital warfare. With cybersecurity researchers and defenders racing against time to thwart malicious actors, vigilance and collaboration remain our most potent weapons.
In the face of APT-level activity, characterized by stealth, sophistication, and state-backed origins, the imperative for enhanced cybersecurity measures has never been clearer. Through continued research, information sharing, and technological innovation, we stand poised to confront and overcome the challenges posed by threats like Kapeka, safeguarding the integrity and security of our digital world.

.png)



.gif)
